Introduction
Cybersecurity is a growing concern amongst business owners in New Zealand and abroad. The New Zealand Government’s Cybersecurity organisation, CERT NZ's latest Report, 4740 cybersecurity incidents were reported in New Zealand over 2019, up 38% from 2018. The total reported financial loss related to these incidents was $16.7 million. This data reinforces the urgent need for internationally acknowledged and independently verified cybersecurity standards.
With comparatively weak regulation concerning organisational level cybersecurity practice, more New Zealand firms are looking to align themselves with industry 'best practice' standards. In the area of data management ISO27001 represents the industry 'gold standard' of independent security standards.
Who is ISO?
ISO27001 is the most widely recognised information security standard of the ISO/IEC 27000 Group. ISO27001 sets the parameters for establishing an information security management system (ISMS). An ISMS is a systematic approach to managing sensitive company information so that it remains secure. Included in the scope of the ISMS are people, processes and information technology (IT) systems, all of which are subject to risk management processes.
Who grants ISO/IEC 27001:2013?
The International Organization for Standardisation (ISO) is responsible for developing the standards but are not involved in the certification. The certification is performed by an ISO accredited independent security body.
ISO/IEC 27001:2013 Section 1
The ISO27001 standard is divided into two sections. The first section consists of 11 clauses with the first four clauses laying the foundations for an ISMS (Introduction, Scope, Normative references and Terms and Definitions).
The following seven clauses outline the requirements organisations must meet to comply with ISO27001.

The majority of the seven clauses are self-explanatory, thus, will not be covered in great depth in this article. However, two clauses are of particular significance as they aid in defining how broad, or narrow, the standard applies to the different aspects of an organisation.
4. Context of the organisation:
Implementing ISO27001 successfully requires firms to understand the scope of their organization and the external and internal issues relevant to the organisation's purpose and their possible impact on the firm delivering the ISMS.
Section 4.3 states firms must determine the boundaries and applicability of the ISMS to establish scope. This later influences whether the standard applies to different parts of the organisation.
5. Leadership
Clause 5 addresses the importance of top management's commitment to the ISMS, acting as leaders who steer the organisation to achieve the ISMS and commit to the continuous improvement of the ISMS in the organisation. Beyond the significant financial resources required to gain and uphold certification, as the ISMS should cover all areas of the firm's operations – leaders must encourage and enforce the standards security management systems across all levels of the organisation.
6. Planning
Taking into account the issues relevant to the organisation identified in clause 4 (Context of the organisation), risks and opportunities must be identified and addressed to ensure the ISMS achieves the intended outcome. Planning remains a critical part of the certification process as it later dictates which of the 114 controls are relevant to the organisation's activities.
7. Support
Organisations should allocate adequate resources and delegate responsibility for the establishment, implementation, maintenance and continual improvement of the ISMS. It is important organisations delegate adequate resources to this as the standard requires annual audits and monitoring to ensure compliance. Often the organisations Chief Security Officer (CSO) will be delegated the lead role in managing and upholding the standard.
8. Operation
Central to successful information security of an organisation is the processes it implements. Processes must be planned, implemented and controlled by top management.
9. Performance Evaluation
ISO 27001 requires continuous monitoring, analysis, and evaluation of the organisation's performance after obtaining the standard. The evaluation consists of the organisation reviewing its performance, top management reviewing the organisation's ISMS and subjecting the organisation to internal audits. This clause is included as an acknowledgement that organisations are constantly adapting and changing, as are the risks relevant to them. Thus, organisations must take a pro-active approach to ensuring their ISMS stays relevant to evolving threats to information security.
10. Improvement
Based on the evaluation of the firm beyond the initial certification, organisations must commit to addressing any non-conformities realised during evaluation and take action to eliminate these causes where applicable. While the certification recognizes an organisations compliance with the ISO27001 standard, the standard requires firms to acknowledge that ‘fool-proof’ security does not exist and organisations should be striving for constant improvement.
The key aspect of the framework - Annex A:
Annex A is one of the most recognised annexes of the entire ISO range of standards. Annex A lists the tools a firm aiming to achieve ISO27001 certification has at its disposal, referred to by the standard as a control.
The standard lists 114 controls which are organized and grouped into 14 distinct domains. Listed below is a brief description of the 14 domains:
· A.6 Organization of information security – controls on how the responsibilities are assigned; also includes the controls for mobile devices and teleworking
· A.7 Human resources security – controls prior to employment, during, and after the employment
· A.8 Asset management – controls related to inventory of assets and acceptable use; also for information classification and media handling
· A.9 Access control – controls for the management of access rights of users, systems and applications, and for the management of user responsibilities
· A.10 Cryptography – controls related to encryption and key management
· A.11 Physical and environmental security – controls defining secure areas, entry controls, protection against threats, equipment security, secure disposal, Clear Desk and Clear Screen Policy, etc.
· A.12 Operational security – lots of controls related to the management of IT production: change management, capacity management, malware, backup, logging, monitoring, installation, vulnerabilities, etc.
· A.13 Communications security – controls related to network security, segregation, network services, transfer of information, messaging, etc.
· A.14 System acquisition, development and maintenance – controls defining security requirements and security in development and support processes
· A.15 Supplier relationships – controls on what to include in agreements, and how to monitor the suppliers
· A.16 Information security incident management – controls for reporting events and weaknesses, defining responsibilities, response procedures, and collection of evidence
· A.17 Information security aspects of business continuity management – controls requiring the planning of business continuity, procedures, verification and reviewing, and IT redundancy
· A.18 Compliance – controls requiring the identification of applicable laws and regulations, intellectual property protection, personal data protection, and reviews of information security
Evidently, the standard’s domains go far beyond the scope of just IT as an information security risk. Figure 1.1 below is a breakdown of the controls and which of the organisation's activities and areas it applies to.
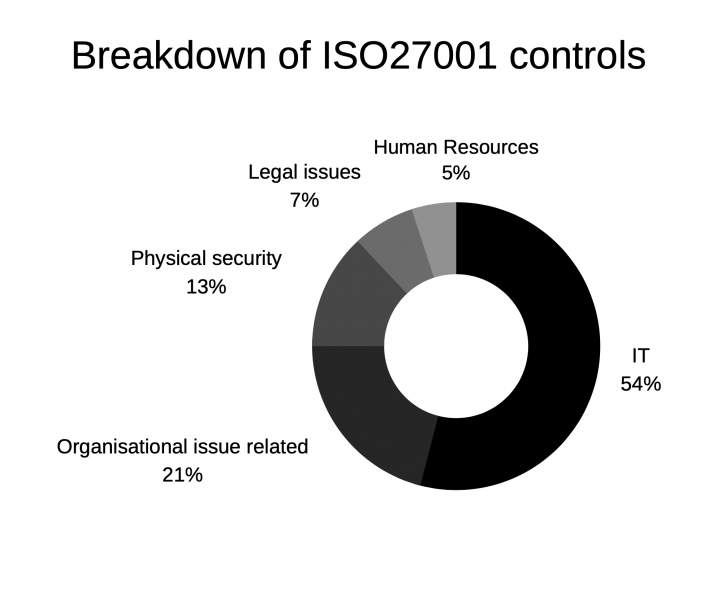
Of course, it is not necessary that firms implement all 114 controls. More so, firms should think ISO27001’s Annex A as a catalogue of 114 controls in which firms select the controls that are applicable to them. An example of best practice selection would be a firm who did not outsource the development of software choosing to not include control 14.2.7 Outsourced Development out of their ISMS. In most cases, 90% of the controls should apply to a firm aiming to achieve ISO27001, but as mentioned in Section 1 Clause 4 firms are able to define how broadly the standard applies to their organisation.
An example of self-selection in practice would be a firm who provides datacentre services as well as cloud services. When determining the context of the organisation, the firm is faced with the decision of including just their data centre in the statement of applicability or both their data centre and managed services.
Critics argue that the element of self-selection the standard firms are allowed opens up scope for abuse of the flexibility, where firms may try to implement the bare minimum number of controls to pass the standard and gain certification for marketing purposes.
Proponents of the standard advise any parties looking to engage in business partnerships or transactions with firms claiming to be ISO27001 certified should always check how broadly the scope of the standard applies to the organisation’s business activities and how many of the standards 114 controls the accredited firm has implemented.
Conclusion
After a brief analysis of the extensive and rigorous ISO27001 standard which sets the parameters for a firm to implement an ISMS, a pattern of prominent overarching principles can be identified. Firstly, the standards' emphasis on the constant evaluation of performance and improvement of the ISMS signifies the notion that firms cannot simply gain their certificate and call it there - as threats adapt and improve, so should firms responsible for sensitive information. Secondly, the standards broad inclusion of factors that pose a risk to an organisations information reinforces the need for buy-in from all of the organisations business units and staff to uphold information security, debunking the common belief that information security is solely the IT departments domain. Finally, the flexibility of the standard allows for firms to devise a concise and relevant ISMS. This flexibility opens the standard up to potential exploitation from firms who may adopt the bare minimum of controls or apply the standard to a small subset of their business activities in order to gain certification for marketing purposes only.